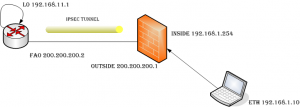
Un semplice laboratorio realizzato per mostrare la creazione di una VPN IPSec utilizzando un PIX 501 e un Cisco 1720.
E’ un laboratorio per poveri, come lo chiamo io, data la poca disponibilità di hw ma quest’ultimo fattore serve anche a stimolare la creatività.
Lo scopo è quello di creare una VPN gateway to gateway, o meglio una IPSec-VPN
viste le molteplici tipologie di VPN presenti oggi sul mercato (L2/3 MPLS VPN, SSL VPN ecc.) e realizzare quindi un tunnel cifrato, utilizzando AES 256, tra i due apparati.
Il portatile e la loopback servono per testare il tunnel, chi ha fantasia può modificare la topologia del laboratorio oppure potrebbe provare a sniffare con ethereal, o whireshark, un ping fatto dal 1720 verso il portatile. Fatelo! Non limitatevi a copiare o testare le configurazioni riportate, fatevi venire qualche idea e provate. Magari sbaglierete ma sicuramente imparerete.
Il laboratorio era stato pensato per un seminario di approfondimento tenuto ad un corso CNAP (Cisco Networking Academy Program) a Genova, avevo fatto una lezione con delle slides sui protocolli alla base di IPSec e poi il laboratorio.
Purtroppo non trovo più le slides. E allora sotto, ora tocca a voi!
Configurazione Cisco PIX 501:
PIX Version 6.3(1) interface ethernet0 auto interface ethernet1 100full nameif ethernet0 outside security0 nameif ethernet1 inside security100 enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted hostname tomcat domain-name gllabs.tk fixup protocol ftp 21 fixup protocol h323 h225 1720 fixup protocol h323 ras 1718-1719 fixup protocol http 80 fixup protocol ils 389 fixup protocol rsh 514 fixup protocol rtsp 554 fixup protocol sip 5060 fixup protocol sip udp 5060 fixup protocol skinny 2000 fixup protocol smtp 25 fixup protocol sqlnet 1521 names name 192.168.11.0 remotelan access-list inside_outbound_nat0_acl permit ip 192.168.1.0 255.255.255.0 remotelan 255.255.255.0 access-list outside_cryptomap_20 permit ip 192.168.1.0 255.255.255.0 remotelan 255.255.255.0 pager lines 24 mtu outside 1500 mtu inside 1500 ip address outside 200.200.200.1 255.255.255.252 ip address inside 192.168.1.254 255.255.255.0 ip audit info action alarm ip audit attack action alarm pdm location remotelan 255.255.255.0 outside pdm logging informational 100 pdm history enable arp timeout 14400 global (outside) 1 interface nat (inside) 0 access-list inside_outbound_nat0_acl nat (inside) 1 0.0.0.0 0.0.0.0 0 0 route outside remotelan 255.255.255.0 200.200.200.2 1 timeout xlate 0:05:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h225 1:00:00 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout uauth 0:05:00 absolute aaa-server TACACS+ protocol tacacs+ aaa-server RADIUS protocol radius aaa-server LOCAL protocol local http server enable http 192.168.1.0 255.255.255.0 inside no snmp-server location no snmp-server contact snmp-server community public no snmp-server enable traps floodguard enable sysopt connection permit-ipsec crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac crypto map outside_map 20 ipsec-isakmp crypto map outside_map 20 match address outside_cryptomap_20 crypto map outside_map 20 set peer 200.200.200.2 crypto map outside_map 20 set transform-set ESP-AES-256-SHA crypto map outside_map interface outside isakmp enable outside isakmp key ******** address 200.200.200.2 netmask 255.255.255.255 no-xauth no-config-mode isakmp policy 20 authentication pre-share isakmp policy 20 encryption aes-256 isakmp policy 20 hash sha isakmp policy 20 group 5 isakmp policy 20 lifetime 86400 telnet timeout 5 ssh timeout 5 console timeout 0 terminal width 80
Configurazione Cisco 1720:
! version 12.3 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname gllabs-maverik ! boot-start-marker boot-end-marker ! ! memory-size iomem 10 no aaa new-model ip subnet-zero ! ! ! ! ip cef ip audit notify log ip audit po max-events 100 ip ssh break-string no ftp-server write-enable ! ! ! ! ! crypto isakmp policy 1 encr aes 256 authentication pre-share group 5 crypto isakmp key CHIAVEIPSEC address 200.200.200.1 crypto isakmp keepalive 12 ! ! crypto ipsec transform-set tset esp-aes 256 esp-sha-hmac ! crypto map ipsecmap 20 ipsec-isakmp set peer 200.200.200.1 set transform-set tset match address 111 ! ! ! ! interface Loopback0 ip address 192.168.11.1 255.255.255.0 ! interface FastEthernet0 ip address 200.200.200.2 255.255.255.252 speed auto crypto map ipsecmap ! ip classless ip route 0.0.0.0 0.0.0.0 200.200.200.1 no ip http server no ip http secure-server ! ! ! access-list 111 permit ip 192.168.11.0 0.0.0.255 192.168.1.0 0.0.0.255 snmp-server community zabbix_monitoring RO snmp-server enable traps tty ! ! control-plane ! ! line con 0 line aux 0 line vty 0 4 login ! no scheduler allocate ! end



